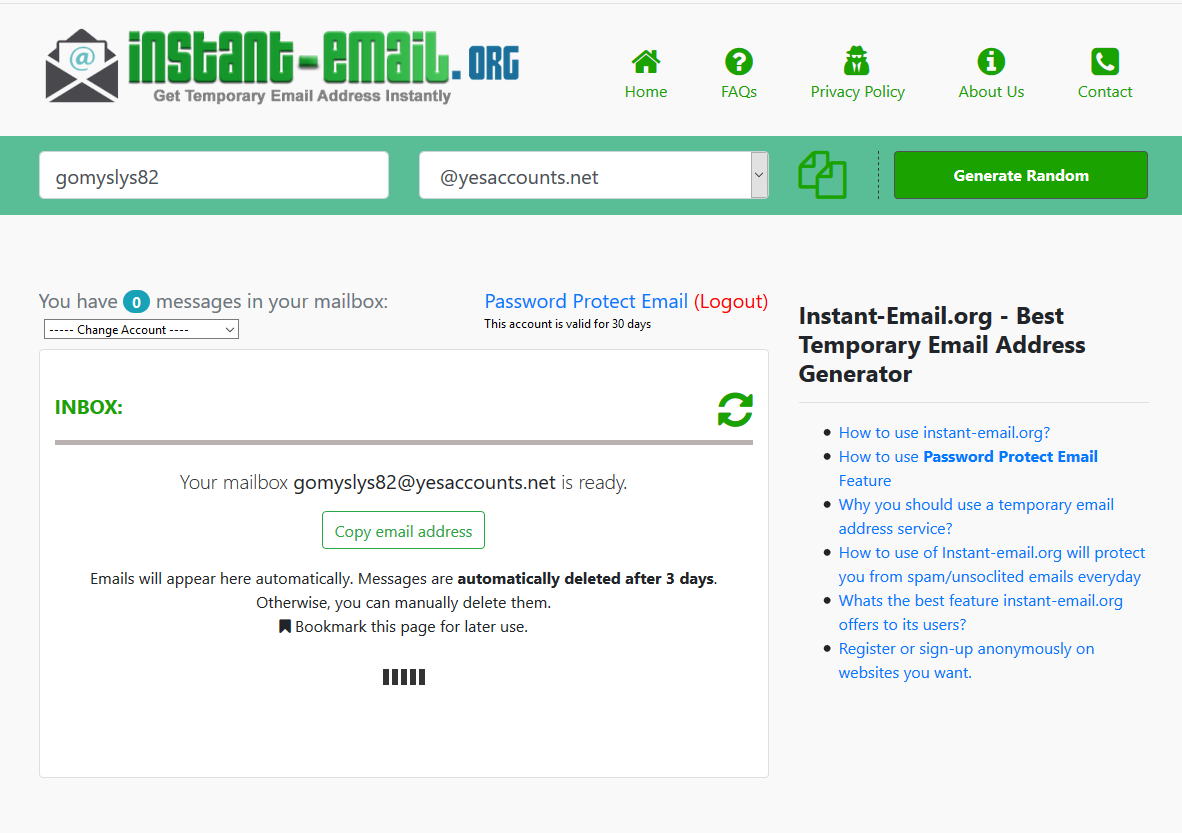
This is Best Way to Avoid Spam on Your MailBox
All of us may have experience wanting to sign up for a website for their free trial, but we are not comfortable providing our personal emails, or getting tired of the spam messages on your personal email because of these here-today-gone-tomorrow websites. Then everyone rejoice, temporary email services is the answer to your worries. Dissimilar … Read more